Computer Networks Questions and Answers
Do you always find yourself searching on the internet. It is actually amazing thinking about the way on how the internet really works. It simply feels like magic the way in which a person could connect to the internet, make their researches, watch out for videos and more. How can this be a thing possible? Well, thanks to the TCP/IP or the Transmission Control Protocol/Internet Protocol.
The TCP/IP have been developed in the year 1978, which has been also driven by Bob Kahn and Vint Cerf. These days, the TCP/IP is also a useful kind of language that governs the communications among the entire computers that are also on the Internet. On the other hand, the TCP/IP is a separate kind of protocols, though they are being used together. The standard of Internet Protocol simply dictates the way on how packets of the information are being set out for over the networks. The internet protocol has its packet-addressing method that mainly lets any sort of computer on the Internet and forward a packet into another computer which is mainly a step or something that is closer into the recipient of the packet.
Moreover, the TCP also makes it sure that the data transmission is also reliable around the networks connected to the Internet.
Tags: Protocols
Have you always connected your net accessible gadgets to the internet? You must have heard IP and already know that it means Internet Protocol. However, do you really have any idea about what it really is? IP is the primary protocol of the network being used online. It has been developed in the year 1970. IP also supports the unique addressing for the computers on a certain network. Most of these networks are using Internet Protocol in version 4 with the standard featuring the addresses that are about 16 bytes in length.
The data on the Internet Protocol network is being organized into the packets. Every IP Packet mainly includes both of the header which is used for specifying the destination, source and any other information regarding the data as well as the data of the message itself. Moreover, the IP simply functions of the third layer of the OSI Model. Thus, it could run on the top of various interfaces of data including WI-Fi and Ethernet. It only means that Internet Protocol is one of the essential matters when it comes to connecting to the internet. Moreover, upon the internet and any other networks, Internet Protocol is frequently used together with the TCP or the Transport Control Protocol and known together as TCP/IP.
Tags: Protocols
So, what are the Network Topologies? In simple sense, they refer to as the network layout and how the varied nodes in the network are connected to each and everyone and on how they communicate as well. Mesh Topology is a kind of Network Topologies in which in a mesh network, the devices are being connected with a whole lot of redundant interconnections in between the network nodes. There are actually two kinds of mesh topologies, here are those:
• Full Mesh – it takes place when each and every node has their own circuit that connects each and every other node into the network. The full mesh topology is somewhat an expensive one to implement, yet it yields a wider redundancy amount. Thus, in the event that one of the nodes had failed, the network traffic could be directed to any other kinds of nodes. Usually, full mesh is reserved only for the networks that serves as the backbone.
• Partial Mesh- it is somewhat less expensive to implement and it only yields very less sort of redundancy than the latter. With such, some of the nodes are being organized in complete scheme, yet the others are only connected to one or two in a certain network.
Knowing more about the essence of Network Topologies could surely help one out.
Simply imagine the number of people who are communicating across the world. They are using up various languages and different machines and even uses up different software in order to transmit data. If there are no standards, communication around the world would never be possible. Well, one of the tools being used for transmitting data is the protocol? So, what is the protocol? It is actually used for the reliable transmission of data for every the network. The HTTP or the HyperText Transfer Protocol being used for transmitting as well as displaying the information in the form of web pages across the browsers on the internet.
On the other hand, there are three kinds of Protocol, here are those:
• TCP- known as the Transmission Control Protocol that uses a good set of rules in order to exchange the messages with any other internet points at the packet level of information.
• IP- known as Internet Protocol that uses a good set of rules in order to send and receive messages at the address level of the internet.
• FTP or HTTP- stands for File Transfer Protocol or Hypertext Transfer Protocol that has their own defined set of rules to use with the corresponding programs anywhere else on the net.
Knowing the different types of protocol could help you understand about on how they are being used.
Tags: Protocols
Do you know what Ben’s Network is and how it works? Well, with Ben’s Network service, they truly appreciate that not all of the companies mainly have he same need when it comes to their IT division. Some actually need a full time tech on-site and others just require a little courtesy once in a week. Whatever you need, they are able to do as much or as little, depending upon what you truly need.
On the other hand, for the larger companies, they are offering the on-site technicians to handle the needs and the software updates of their users. With the backing of the other root of the technicians as well as computer upgrades on the larger scale, they are sure enough to help you with everything that you need. They even assist desk to work with the users for faster resolution and rental computers and printers whenever your unit is in need of repair.
For those of the medium sized companies, they are offering great assistance for the employees and go back to it together with the tools in order to keep you running with great options in terms of help desk, computer as well as printer rentals. The monthly service plan on the equipment as well as upgrade and even rollout testing for the compatibility of the pre-upgrade.
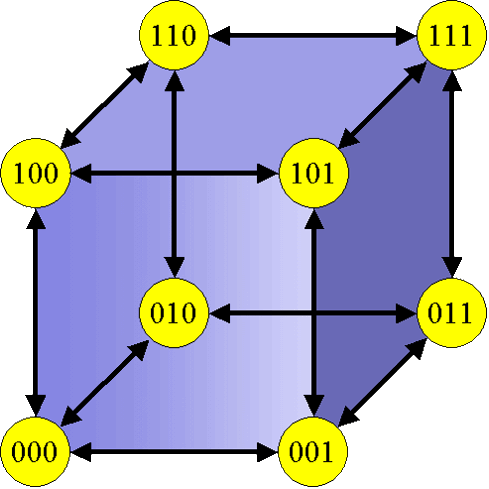
Image Source: cs.virginia.edu
Developments in hardware technology have made it feasible to fabricate a large scale multiprocessor system which holds tens of thousands of processors. One vital measure on planning such a multiprocessor system is to establish the topology of the interconnection, because the system operation is extensively affected by the network topology.
Generally when a n-dimensional grid network is linked circularly in more than a single dimension, the consequential network topology is a torus, and the resultant network is known as toroidal. When the number of nodes along each dimension of a toroidal network is two, the consequential network is described as a hypercube.
The binary n-cube, additionally known as the hypercube network has been confirmed as an extremely powerful topology. Hypercube is the most extensively benefited from topology for the reason that it offers small diameter, that is the greatest number of links (or hops) a message has to pass through to achieve its ultimate destination between any two nodes. It also implants a variety of interconnection networks. For exceptionally huge systems though, the number of links required by the hypercube could turn out to be prohibitively large.
The main limitation of the hypercube network is its lack of scalability, which restricts its application in constructing bulky systems out of small size systems with modest of alterations in its configuration.
The TCP/IP is one of the highly used network protocols, these days. However, do you have any idea about what network protocol really is? Well, protocol is like a language being used to make two computers talk to each other. Just like in the real world, if ever they don’t talk the same language, they are not able to communicate.
On the other hand, the TCP/IP is not actually a protocol, yet it is a set of protocol. It is actually known as the Protocol stack, as what it has been commonly known. For instance, it already refers to two variable protocols, the TCP an the IP. Moreover, on the internet layer, you have the Internet Protocol or the IP that gets the packets being received from the Transport Layer and add up virtual address information, just like adding the computer address that is sending the data and the address of the computer that will then receive the data. All of these virtual addresses are known as the IP Addresses. After then, the packet will be sent into the lower layer, called as the Network Interface. With this layer, the packets will be known as the datagrams. The packets that are also transmitted over the network are then known as the frames.
Well, it is not for industrial matters, as it is more of a computer related tool. A bridge is a sort of device separating two or more network segments within a certain logical network. Usually, a bridge is being placed in between two separate groups of computers talking with each other, yet not that much with those of the computers in any other group. A good instance of this is to mainly consider a good cluster of Mac and Unix machines.
These groups of machines would tend to be somewhat chatty among itself and the traffic that they are producing on the network mainly roots impacts of the other technologies who are also trying to speak up to one another. The main task of a bridge is that, it examines the endpoint of the data packets at a time and mainly decide whether or not they could pass down the packets into the other side of the Ethernet segment. Thus, the result is somewhat faster and much quitter network without too much of collisions.
Keep in mind that it is essential to understand the bridge could be somewhat a firewall or a router. In a much simpler tern, a bridge mainly behaves just like a network switch, making it a transparent network component.
Securing wireless network is an essential thing, for the reason that, if you don’t, your neighbors could not just borrow your internet connection, but it could also gain access to your files and simply check on what you have been doing. In the worse case scenario, the hackers could get their most awaited chance to use up your internet connection and upload illegal materials, thus making you liable of something that you did not really do.
Enabling the encryption upon your access point. Using the 128-bit encryption or higher than that will definitely make your Wireless Network in a much secure. The WPA and the WPA are schemes with different encryption. The WEP has been proven to be insecure and could be cracked in just a matter of minutes, by just using the tools that could be freely downloaded from the net. Using WPA is however, a recommended one. This is for the reason that it is something that is a lot more secure, yet it could be sometimes harder to set correctly than what the WEP is and is far more secure. Some of the access points that are already older or those of the wireless cards do not mainly support WPA2. If ever you have one of such, it is somewhat recommended that you purchase a newer one supporting the WPA2.
The MAN or the Metropolitan Area Network is a kind of network interconnecting the users with the computer resources in the geographic area or region that is larger than the covered by a large local area network, yet smaller than the area covered by wide area network. The term is being applied to the interconnection of the networks into the city in a single larger network that offers efficient connection to the wide area network. It is even used as the interconnection of some local area networks by mainly associating them with the support lines. The end usage is also referred to as the campus networks.
Some examples the metropolitan area networks of different sizes could be originated in the urbanite areas of London, England, Geneva, Poland, Lodz and Switzerland. The large universities also use the terms in order to describe their networks. The recent trend is mainly the installation of wireless MAN. The working mechanism of the MAN is somewhat similar to the ISP or Internet Service Provider, yet a MAN isn’t owned single organization. Just like a WAN, a MAN mainly provides shared connections of the network to its users. Mostly, the MAN works on the layer of the data link, which is Layer 2 of the Open Systems interconnection model.

